Below is a list of the most frequently used modules and commands in Volatility3 for Windows.
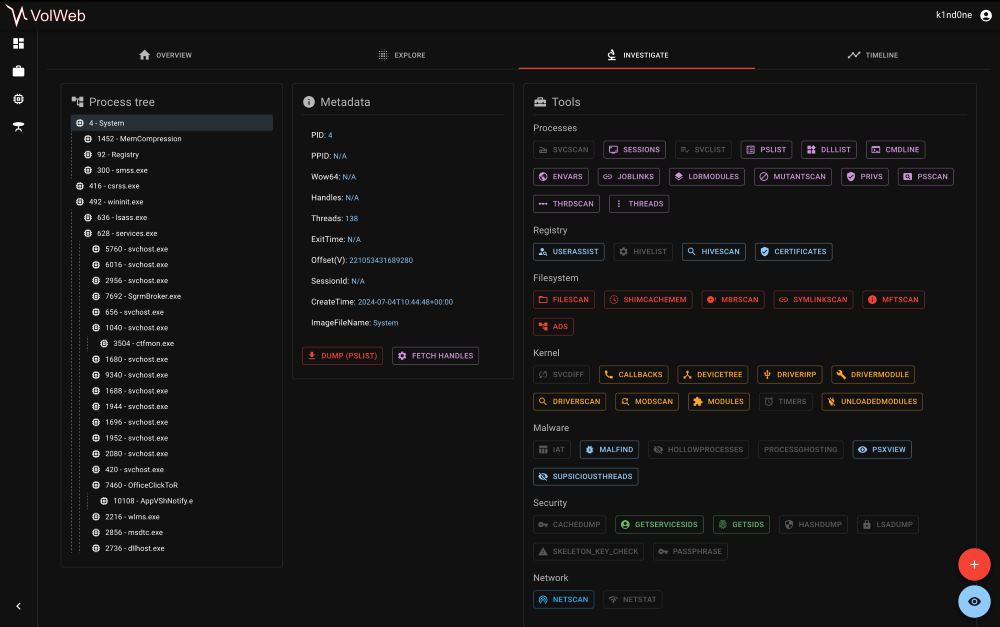
Web UI
VolWeb is a powerful user interface for volatility 3 :
OS
OS information
volatility -f "/path/to/image" windows.info
Environment variables
volatility -f "/path/to/image" windows.envars
Connected users
volatility -f "/path/to/image" windows.sessions.Sessions
Show registers
volatility -f "/path/to/image" windows.registry.hivescan
List roots :
volatility -f "/path/to/image" windows.registry.hivelist
List roots and get initial subkeys :
volatility -f "/path/to/image" windows.registry.printkey.PrintKey
Print Key :
volatility -f "/path/to/image" windows.registry.printkey.PrintKey --key "Software\Microsoft\Windows NT\CurrentVersion"
List services
volatility -f "/path/to/image" windows.svcscan.SvcScan
List scheduled tasks
volatility -f "/path/to/image" windows.registry.scheduled_tasks.ScheduledTasks
Find executed commands
volatility -f "/path/to/image" windows.cmdline
Commands entered in cmd.exe are processed by conhost.exe (csrss.exe before Windows 7). So even if an attacker has managed to kill cmd.exe before we get a memory dump, there’s still a chance of recovering the command line history from conhost.exe’s memory. If you find something odd, try dumping the memory of the process associated with conhost.exe and look for strings inside to extract the command lines
Processes / Programs
List processes
volatility -f "/path/to/image" windows.pslist
volatility -f "/path/to/image" windows.psscan
volatility -f "/path/to/image" windows.pstree
Environment variables
volatility -f "/path/to/image" windows.envars --pid <PID>
Dump process memory
volatility -f "/path/to/image" -o "/output/path" windows.memmap.Memmap --pid <PID> --dump
Dump the dlls & exe associated with a process
volatility -f "/path/to/image" -o "/path/to/dir" windows.dumpfiles ‑‑pid <PID>
Extract a process’s memory pages
Extract all pages stored in memory into a single file.
volatility -f "/path/to/image" -o "/path/to/dir" windows.memmap ‑‑dump ‑‑pid <PID>
Extract the “Handles” of a process
volatility -f "/path/to/image" windows.handles ‑‑pid <PID>
A handle is a structure that lets you define an object (file, socket, pipe, shared memory area, etc. ) and then manipulate it. Handles can be shared by several processes.
DLLs loaded by a process
volatility -f "/path/to/image" windows.dlllist ‑‑pid <PID>
volatility -f "/path/to/image" windows.ldrmodules.LdrModules --pid <PID>
Unloaded DLLs
volatility -f "/path/to/image" windows.unloadedmodules
Network
Show network connections
volatility -f "/path/to/image" windows.netscan
volatility -f "/path/to/image" windows.netstat
Files
List files
volatility -f "/path/to/image" windows.filescan
Extract files
All files found
volatility -f "/path/to/image" -o "/path/to/dir" windows.dumpfiles
From its virtual memory offset :
volatility -f "/path/to/image" -o "/path/to/dir" windows.dumpfiles ‑‑virtaddr <offset>
From its physical memory offset :
volatility -f "/path/to/image" -o "/path/to/dir" windows.dumpfiles ‑‑physaddr <offset>
Malware analysis
Suspicious memory spaces:
volatility -f "/path/to/image" windows.malfind
# YARASCAN
volatility -f "/path/to/image" windows.vadyarascan ‑‑yara-rules <string>
volatility -f "/path/to/image" windows.vadyarascan ‑‑yara-file "/path/to/file.yar"
volatility -f "/path/to/image" yarascan.yarascan ‑‑yara-file "/path/to/file.yar"
Function calls
windows.iat.IAT --pid <PID>
Direct system call (hooking bypass)
# requires capstone to operate
volatility -f "/path/to/image" windows.direct_system_calls.DirectSystemCalls | grep <PID>
System call table
volatility -f "/path/to/image" windows.ssdt.SSDT
Suspicious threads injection
- Look for thread with
Win32StartAddress = N/A - Look for threads do not have a
Win32StartAddressin the same memory spaces as others - Look for suspicions
Win32StartPathorStartPath(‘-’,suspicious dll)
volatility -f "/path/to/image" windows.suspicious_threads --pid <PID>
volatility -f "/path/to/image" windows.threads| grep <PID>
Suspended threads
volatility -f "/path/to/image" windows.suspended_threads.SuspendedThreads | grep <PID>
DLL injection
- Look for DLLs with supiscious MappedPath
- If MappedPath is N/A, the memory region may have no clear backing on disk (could be injected shellcode or manually mapped DLLs)
- InLoad, InInit and InMem = False (This means the module is not linked into any of the expected DLL lists)
volatility -f "/path/to/image" windows.ldrmodules.LdrModules --pid <PID>
Hollowed processes
volatility -f "/path/to/image" windows.hollowprocesses
Mutex
volatility -f "/path/to/image" windows.mutantscan.MutantScan
Memory pages
volatility -f "/path/to/image" windows.vadwalk.VadWalk --pid <PID>
volatility -f "/path/to/image" windows.vadinfo.VadInfo --pid <PID>
Kernel persistance
volatility -f "/path/to/image" windows.driverscan
# Identify potential drivers hidden by rootkits
volatility -f "/path/to/image" windows.drivermodule.DriverModule
volatility -f "/path/to/image" windows.callbacks.Callbacks
#Hidden kernel modules
volatility -f "/path/to/image" windows.modscan
volatility -f "/path/to/image" windows.driverirp.DriverIrp
volatility -f "/path/to/image" windows.devicetree.DeviceTree
Secrets
Dumps user hashes from memory
volatility -f "/path/to/image" windows.registry.hashdump.Hashdump
Dumps lsa secrets from memory
volatility -f "/path/to/image" windows.registry.cachedump.Cachedump
volatility -f "/path/to/image" windows.registry.lsadump.Lsadump
TrueCrypt Cached Passphrase
volatility -f "/path/to/image" windows.truecrypt.Passphrase
Others
Artefacts
volatility -f "/path/to/image" windows.shimcache
volatility -f "/path/to/image" windows.registry.amcache.Amcache
# Scans for MFT FILE objects present memory
volatility -f "/path/to/image" windows.mftscan.MFTScan
# Scans for Alternate Data Stream
volatility -f "/path/to/image" windows.mftscan.ADS
# Scans for and parses potential Master Boot Records (MBRs)
volatility -f "/path/to/image" windows.mbrscan.MBRScan
# Scans for MFT Records with Resident Data
volatility -f "/path/to/image" windows.mftscan.ResidentData
Certificates in the registry’s Certificate Store
volatility -f "/path/to/image" windows.registry.certificates.Certificates
String search
strings -n <min-string-size> <binary>
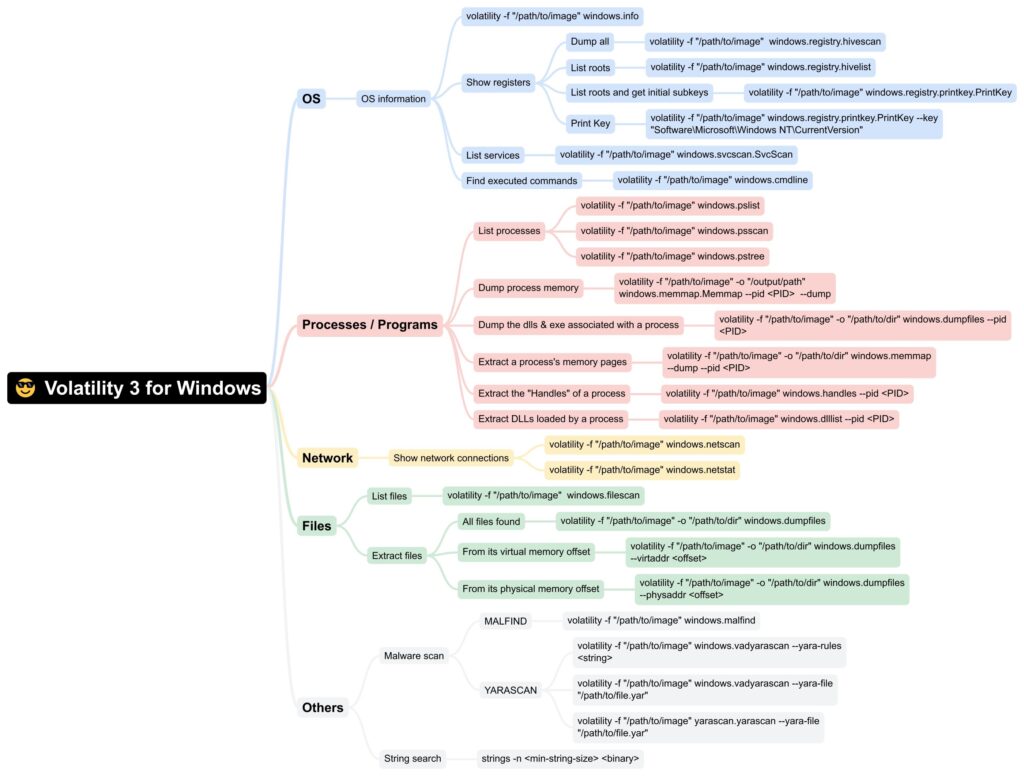
Mindmap
Sources
- Problems with volatility 3 : https://blogs.jpcert.or.jp/en/2021/09/volatility3_offline.html
- Identify profile : https://heisenberk.github.io/Profile-Memory-Dump/
- https://book.hacktricks.xyz/forensics/basic-forensic-methodology/memory-dump-analysis/volatility-examples
- https://blog.onfvp.com/post/volatility-cheatsheet/
- https://book.hacktricks.xyz/generic-methodologies-and-resources/basic-forensic-methodology/memory-dump-analysis/volatility-cheatsheet?q=volatility+
- Convert Markdown to mindmap with Markdown-map.com

1 reply on “ Volatility 3 – Windows | Cheatsheet ”
Comments are closed.